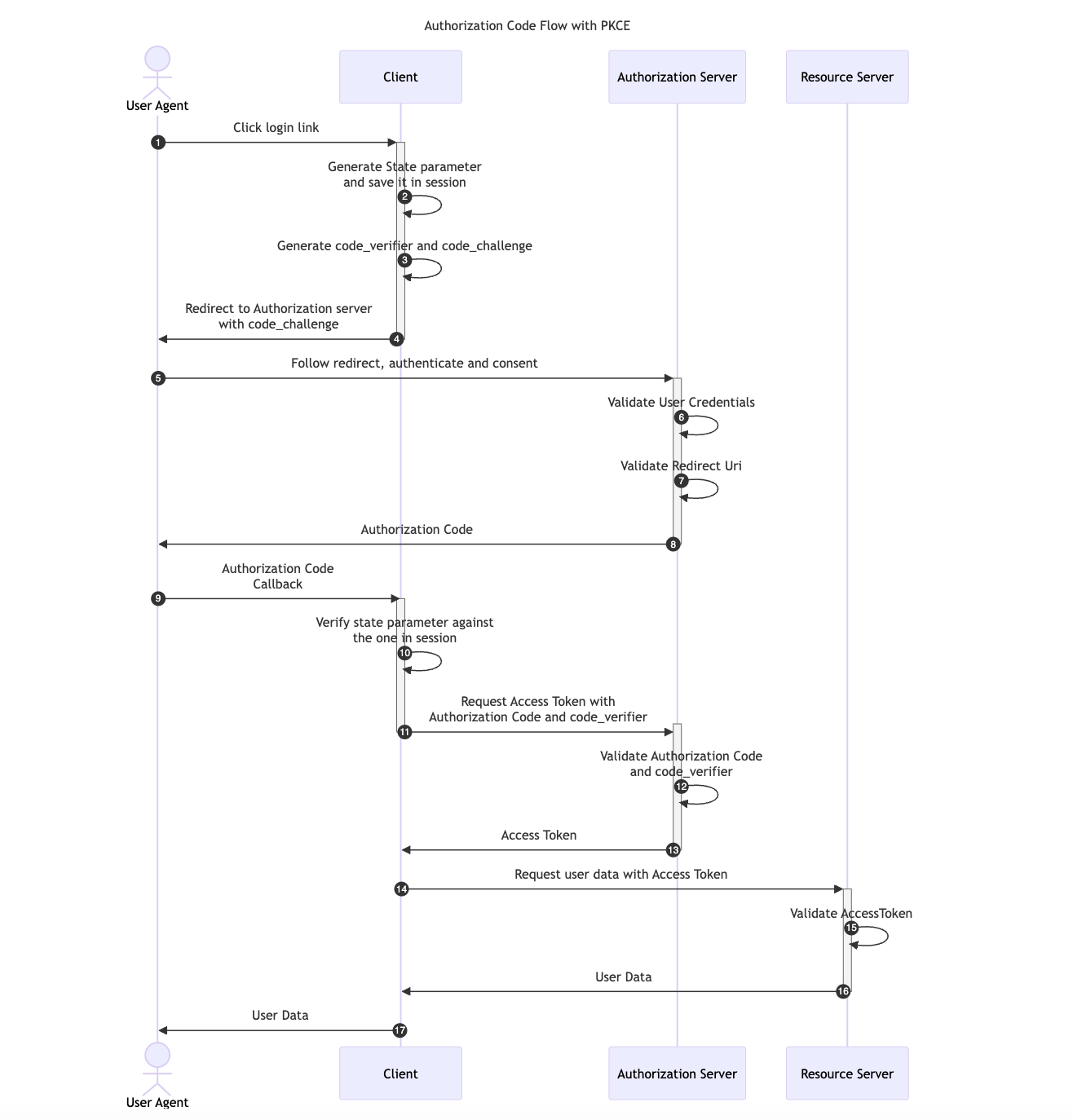
This OAuth flow was designed for applications that cannot store a Client Secret, such as native or single-page apps
Secure way for Implicit Grant
Two new parameters are added to the default Authorization Code Flow, a random generated value called code_verifier and its transformed version, the code_challenge.
- First, the Client creates and records a secret
code_verifierand derives a transformed versiont(code_verifier), referred to as thecode_challenge, which is sent in the Authorization Request along with the transformation methodt_mused. - The Client then sends the Authorization Code in the Access Token Request with the
code_verifiersecret. - Finally, the Authorization Server transforms
code_verifierand compares it tot(code_verifier)